How to get the custom name as standard name in the overview page of Host compliance ?
This article provides you the steps that can be followed to get the custom name as standard name on the overview page of the host compliance as shown below.
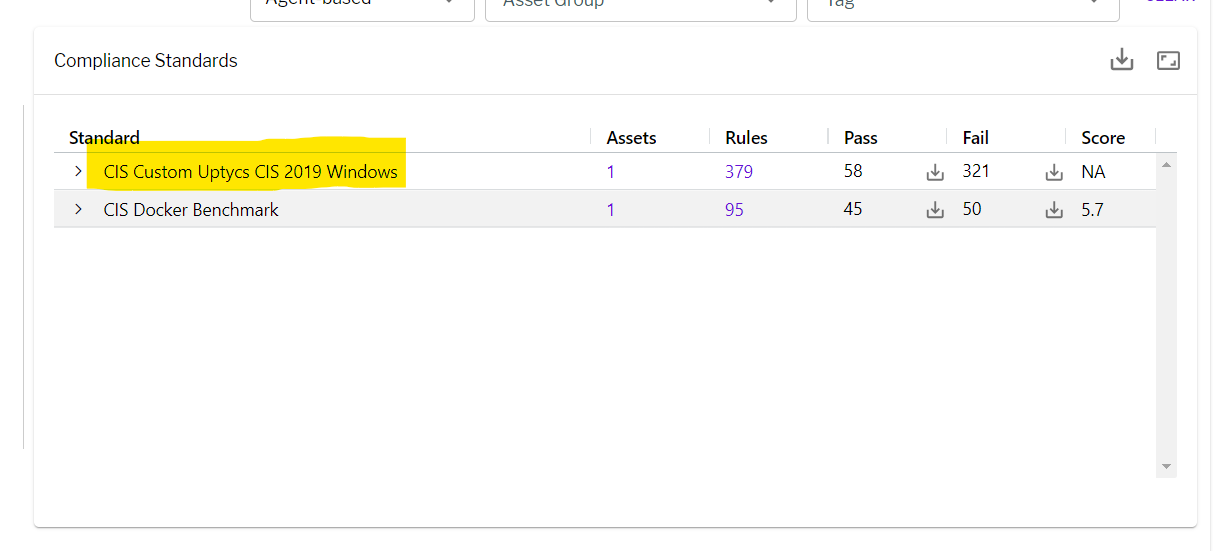
1. To land on compliance overview page , go to Uptycs EDR --> Audit --> Compliance .
2. Then go to Configuration --> Select Uptycs configurations .

3. Here you can select one of the Uptycs custom configuration based on the required operating system and clone the configuration (this will change the Framework to Custom).
4. Now you can change the name and standard (which can be used while investigating in real-time) and save the configuration.
5. Go to custom configurations in the bottom of the page , Click on edit and upload a CSV file containing the compliance checks that you want to configure .In the CSV file the given standard name will be displayed in the overview page which can be edited in the CSV file as required.
1. To land on compliance overview page , go to Uptycs EDR --> Audit --> Compliance .
2. Then go to Configuration --> Select Uptycs configurations .

3. Here you can select one of the Uptycs custom configuration based on the required operating system and clone the configuration (this will change the Framework to Custom).
4. Now you can change the name and standard (which can be used while investigating in real-time) and save the configuration.
5. Go to custom configurations in the bottom of the page , Click on edit and upload a CSV file containing the compliance checks that you want to configure .In the CSV file the given standard name will be displayed in the overview page which can be edited in the CSV file as required.
6 . Make sure to attach the compliance configuration to the asset in settings page .
Related Articles
How should I configure custom Jira fields when creating a Jira destination?
When setting up a Jira destination, the Custom Jira Fields section must be populated with the required custom fields from the linked Jira account in JSON format. These fields are mandatory for the creation of a ticket, even though standard fields ...Difference Between Disk Scan and Malware Scan
Introduction This document provides a comprehensive understanding of the differences between Disk Scan and Malware Scan in Uptycs. Both scans serve different purposes and operate using distinct methodologies. Malware Scan Overview A Malware Scan ...How to obtain an API Key
Overview An API key & secret are used to authenticate API clients to access Uptycs related resources. An API key / secret is unique to individual users. The document describes the process to obtain the same on Uptycs eco-system. Procedure Login into ...Software Catalog Q&A
Software Catalog Q&A 1)Which type of System will be applicable? A)It will be catalog only for Server workloads and systems which have processes running longer than 6 hrs. 2)What is the frequency of cataloging? A)12 Hrs 3)Can we Change the frequency ...What is the SUNBURST Backdoor Intrusion and How Can I detect it?
Overview What is the SUNBURST backdoor intrusion and how can I detect it? FireEye discovered a supply chain attack trojanizing SolarWinds Orion business software updates in order to distribute malware called SUNBURST. This intrusion campaign is ...